Open-Source Adversary-in-the-Middle Phishing Kit Gaining Popularity among Cybercriminals
Microsoft Threat Intelligence has identified an emerging threat actor, DEV-1101, behind the development of an open-source adversary-in-the-middle (AiTM) phishing kit that is gaining popularity among cybercriminals due to its ability to conduct large-scale attacks.
AiTM phishing attacks involve intercepting a target's password and session cookies by deploying a proxy server between the user and the website, causing them more effective in bypassing multi-factor authentication (MFA) protections. DEV-1101 is responsible for several phishing kits that can be purchased or rented by other criminal actors, lowering the barrier of entry for cybercrime.
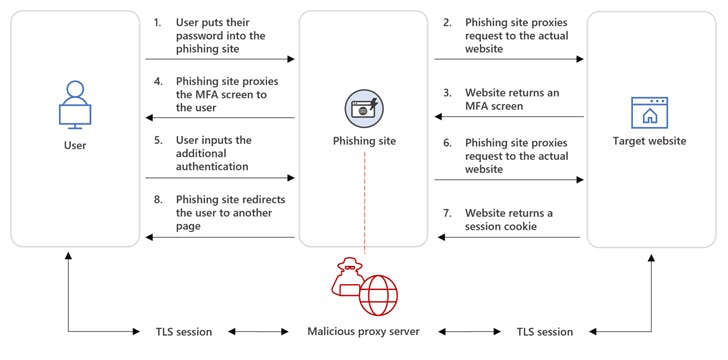
The open-source kit arrives with features that make it attainable to set up phishing landing pages that mimic Microsoft Office and Outlook, address campaigns from mobile devices, and bypass detection using CAPTCHA checks. The service, priced at $300 for a monthly licensing fee and $1,000 for VIP licenses, has undergone several enhancements, including the ability to manage servers running the kit through a Telegram bot.
Microsoft has detected numerous high-volume phishing campaigns, including one from DEV-0928, one of DEV-1101's more prominent patrons, comprising over one million emails since September 2022. The phishing campaign commences with document-themed email messages containing a link to a PDF document, directing the recipient to a login page that masquerades as Microsoft's sign-in portal but not before urging the victim to complete a CAPTCHA step.
Organizations must adopt phishing-resistant authentication methods such as FIDO2 security keys to block suspicious login attempts and protect against AiTM phishing attacks. The availability of such phishing kits for purchase by attackers is part of the industrialization of the cybercriminal economy, which can result in double theft, with the stolen credentials sent to both the phishing-as-a-service provider and their customers.
Thank you for reading our blog. Follow us on social media for more updates and feel free to contact us with any questions or comments. Share with your friends and family. We appreciate your support and look forward to sharing more valuable insights with you.